This post explains how can we identify the model of a wireless router using Linux.
Step by step
1. Set your wireless adapter in monitor mode
Check this post about how to put a wireless adapter in monitor mode in Linux.
This step includes identifying the ID of the wireless you are going to put in monitor mode. We need this reference for further steps on this post, so ensure you write it down. Example: wlan0.
2. Identify the BSSID of the network whose router model you want to identify
Open a terminal and run this command:
sudo airodump-ng wlan# -M --wps
You must substitute the hash symbol in wlan# by the ID of wireless device in monitor mode you have set in the previous step.
After this command is executed, the terminal screen will be updated with a table where each row is a wireless access point nearby your computer.

The meaning of the columns displayed is the following:
- BSSID: Hexadecimal network identifier. It has format 12:34:56:78:90:1B:CD:EF.
- PWR: Power. It is usually a negative number. The closest to zero, the strongest.
- Beacons
- CH: Channel.
- MB
- ENC: Encryption. Example: WPA2
- Cipher: cipher. Example: CCMP
- Auth: Authentication. Example: PSK
- WPS
- ESSID: Text-form network identifier. Example: TP-LINK_ABCD
- MANUFACTURER: Router manufacturer.
The AP’s on the top are the ones closest to you.
Note down the values on the row of the AP whose router model you want to identify.
3. Switch channel to the one used by target
Use this command to switch the channel:
sudo iw wlan# set channel <channel number>
Remember you must substitute:
wlan#by the ID of the wireless device you have in monitor mode. Example: wlan0.<channel number>by the channel number assigned to the router model you want to identify. This value was obtained in the previous step. Example: 5.
Example:
sudo iw wlan0 set channel 1
4. Filter packets with Wireshark
Open Wireshark. You can double click on the Wireshark application icon or by typing this command on the terminal:
wireshark
If you have not installed Wireshark, you can install it from the Ubuntu Software Center or by typing this command on the terminal:
sudo apt-get install wireshark
Once Wireshark is open, select the interface on main screen; again, it would by the ID of the wireless device you have set in monitor mode. Example: wlan0.
At this point, you may received a warning stating that “The capture session could not be initiated on interface ‘wlan#’ (You don’t have permission to capture on that device).”. If this is the case, follow the instructions to avoid this error.

In my case (as I was using Ubuntu), it was solved by typing:
sudo dpkg-reconfigure wireshark-common
I selected option “Yes”.
After doing this, I stop seeing the interfaces when opening Wireshark. I solved it by executing Wireshark as root:
sudo wireshark
Once you have selected the interface and it is confirmed that capture session can be initiated, packets will start to be captured automatically.
You can start by filtering the packets specific to the target network:
wlan.ssid == "<ESSID>"
Remember to substitute <ESSID> by the ESSID found in the second step. Example: TP-LINK_ABCD
On each packets, there are usually Vendor Specific tags. Check them to try to get information about the router.
Try to packets using this filter:
(wps.device_name != "" || wps.model_name != "" || wps.model_number != "") && wlan.ssid == "<ESSID>"
Not all routers provide this information, so you may find no results.
Inside the found frames, look for “Tag: Vendor Specific: Microsof: WPS”. In the fields “Model Name”, “Model Number” and “Device Name” you will notice information about model of the AP.
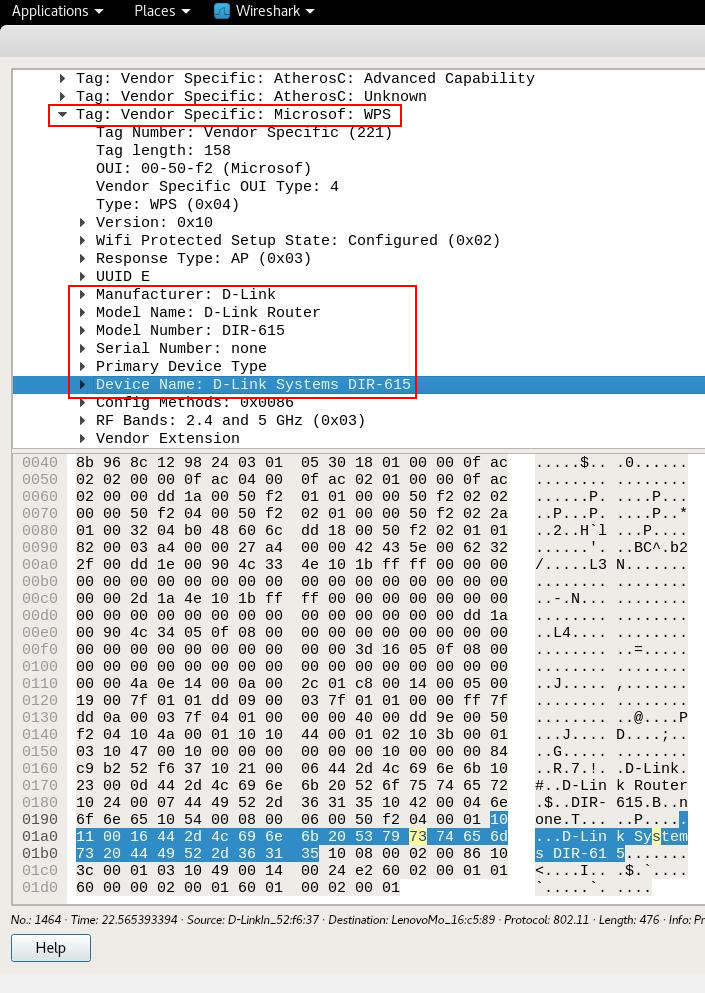
I found that some of the results found display fake data. For example, some broadcom routers display fake values like the ones display below:
- Manufacturer: Broadcom
- Model Name: Broadcom
- Model Number: 123456
- Serial Number: 1234
In any case, there is nothing to lose by checking with this method if there is any relevant information about the packet.
External references
- “How to find out the exact model of a router (wireless access point)“; Alex; miloserdov.org; 2017-09-26.