Types of network segments
According to its privacy, there are different types of network segments:
- Public networks
- Internet
- Private networks
- Extranet
- Intranet
The internet is publicly available for any user.
An intranet hosts information privately only for users within an organization. The services are placed on internal servers.
An extranet is a cross between the internet and an intranet. It acts as an intranet for the private network but also serves information to outsider or external entities. In some cases, it restricts the information to some specific users.
Firewall Architectures
There are these main firewall architectures:
- Screened Host
- Dual-Homed Host
- Screened Subnet
They are explained in further detail below.
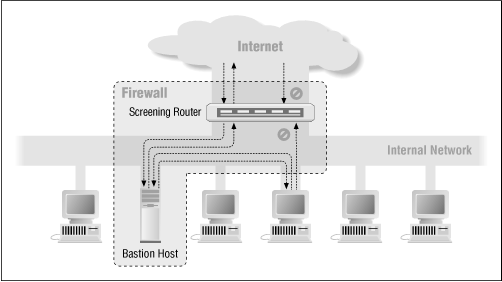
Screened Host Architecture
Screened host architecture consists of two elements
- Packet-filtering or screening router
- Bastion host
The packet filtering router has a set of rules configured that allow inboud traffic to access only the bastion host, which blocks access to internal system.
In this case, the inside hosts reside on the same network as the bastion host. Depending on security configuration and policy, hosts may access internet directly or use proxy services on the bastion host.
An intruder has to penetrate two separate systems before the security of the private network can be compromised.
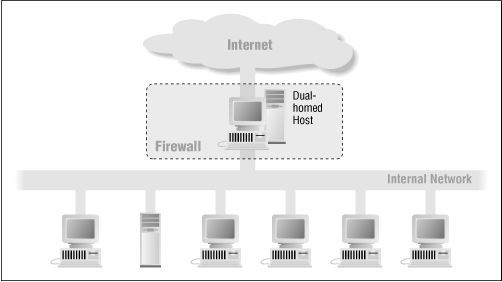
Dual-Homed Host Architecture
Dual-homed host architecture, is also known as bastion host.
The firewall has two or more network interfaces, each of which is connected to a different network. It blocks or filters the traffic between these networks.
Dual-homed firewall is a restrictive form of a screened-host firewall.
Screened Subnet Architecture
A screened subnet is a special-purpose extranet.
In this scenario, the firewall(s) separate(s) 3 distinct zones:
- Internet
- Screened subnet a.k.a. perimeter network a.k.a. demilitarized zone (DMZ) a.k.a. secure server security segment
- Intranet a.k.a. internal network a.k.a. private network
The screened subnet architecture can be designed:
- As a single multi-homed firewall, a.k.a. three-ledged network
- As a dual firewall
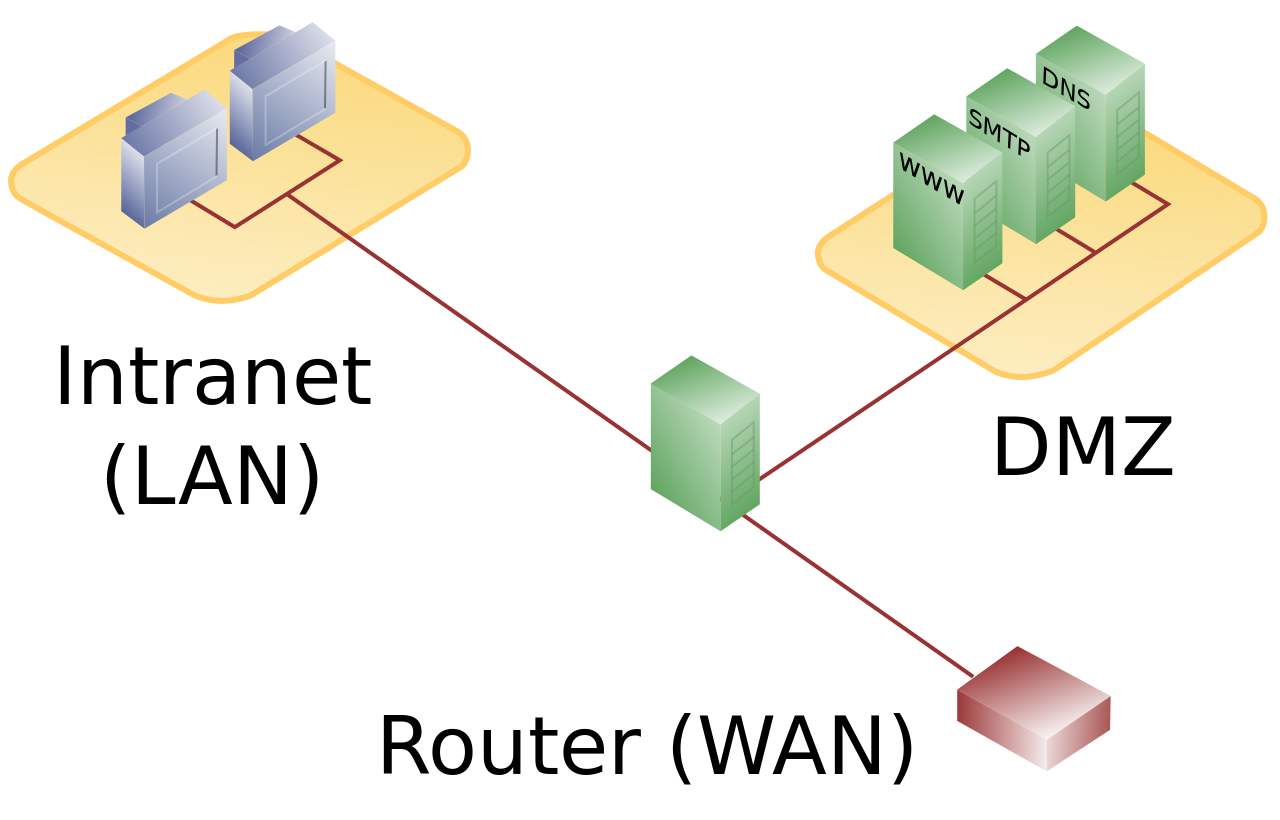
A multi-homed firewall has three interfaces, one pointing the internet, the second a screened subnet and a third the intranet.
This figure shows a network using a single firewall:
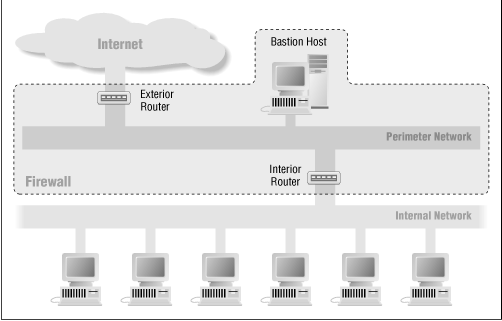
The dual firewall consists of three devices:
- Packet filtering outside router, connecting the internet and the screened subnet
- Bastion or screened host, located in the screened subnet
- Packet filtering internal router, connecting the screened subnet to the intranet
Bastion host acts as a proxy for the trusted systems within the private network. It is responsible for filtering traffic coming into the private network as well as for protecting the identity of the internal system.
External systems can access only the bastion host (and its proxying capacities to internal systems) and possibly information servers in the screened subnet.
Oubound traffic requires the proxy services of bastion host. Filtering rules on the outside router accepts only outbound traffic on the bastion host.
Benefits of screened subnet architecture:
- An intruder must penetrate three separate devices (instead of one or two of the other architectures)
- Private network addresses are not disclosed to the internet
- Internal systems do not have direct access to the internet
This figure shows a network using dual firewall:
Where to place a Server
Servers are place in a different zone depending to whom they are providing services:
- Servers that offer services to the public (e.g. Web servers, SMTP servers) are placed in the screened subnet.
- Servers that offer services to internal users reside on the intranet.
Inbound connections from the Internet are allowed only to servers in the screened subnet; no direct connections are allowed between the Internet and the private network.
Screened subnet / Demilitarized Zone (DMZ)
A Demilitarized Zone (DMZ) is an isolated network used to permit outsiders to access certain corporate information in a semi-trusted environment. The DMZ may host a web server or other external facing services. Traffic to a DMZ is not usually encrypted unless it is terminating on a VPN located in the DMZ.
Placing a Intrusion Detection System
When placing an intrusion detection system (IDS) inside this structure, the best place to set it is on the screened subnet, i.e. DMZ, perimeter network. Some comments regarding placing the IDS in alternative parts of the network:
- Outside the firewall, on the internet side, or on the external router is not usually advised because the system will alert about all malicious traffic, though 99% is stopped by the firewall and never reach the internal network. These options are only recommended when it is required to assess the traffic hitting the firewall.
- The firewall server should be hardened server with minimal services enabled. Because of this, it is not recommended to install the IDS on it.
Placing an Intrusion Prevention System
Traffic must be decrypted prior to being processed by the IPS to allow it to view. The encryption should be terminated at a hardware Secure Sockets Layer (SSL) accelerator or virtual private network (VPN) server to allow all traffic to be monitored.
Connecting through VPN
When connecting through a VPN to the network, VPN tunnels should terminate into a screened subnet that let users have minimum access. Some comments regarding the alternative methods of terminating VPN in a screened subnet:
- Terminating the VPN at the edge router allows traffic to reach servers outside the firewall and possibly inside the firewall, depending on the configured policy, but this solution can eat up resources on a device that is usually designed to pass packets as quickly as possible.
- Terminating a VPN tunnel at the firewall, however, allows direct access to the internal or perimeter network but could actually lower the security posture of the internal network if not configured well and can use up resources on the firewall, which could slow down processing of all traffic leaving your network.
- The last option is using a dedicated VPN appliance, which could require some extra attention to make sure it is implemented in a secure fashion; this is an additional expense when most companies already have edge routers and firewalls, but it allows for larger VPN infrastructures to be built without placing a burden on other devices in the network.
CISA Questions related to firewall architectures
11th Edition: A5-100
You might also be interested in…
External references
- “Firewall architectures“, mik.ua docstore
- ISACA; “CISA Reviw Manual, 26th Edition”, ISACA, pp. 369-370
- ISACA; “CISM Review Manual, 15th Edition“, question 3-1A, ISACA, 2016, pp. 139-140,
- ISACA; “Cybersecurity Fundamentals Study Guide, 2nd Edition“, ISACA, 2017, pp. 65
- Mike Chapple; “How do a DMZ and VPN work together?“, TechTarget
- Ido Dubrawsky et al., “Designing and building enterprise DMZ“, Elsevier, 2006
- EC-Council; “Certified Ethical Hacker v10. Module 12: Evading IDS, Firewalls, and Honeypots”, EC-Council, 2018, slide 10 “Firewall Architectures”
- M. Chapple, Stewart, Gibson; “CISSP Study Guide Ninth Edition”, pp. 545-546; Wiley, 2021